
Templates Community /
App with 2 Firewall DMZ
App with 2 Firewall DMZ
Lind Simnica
Published on 2021-11-28

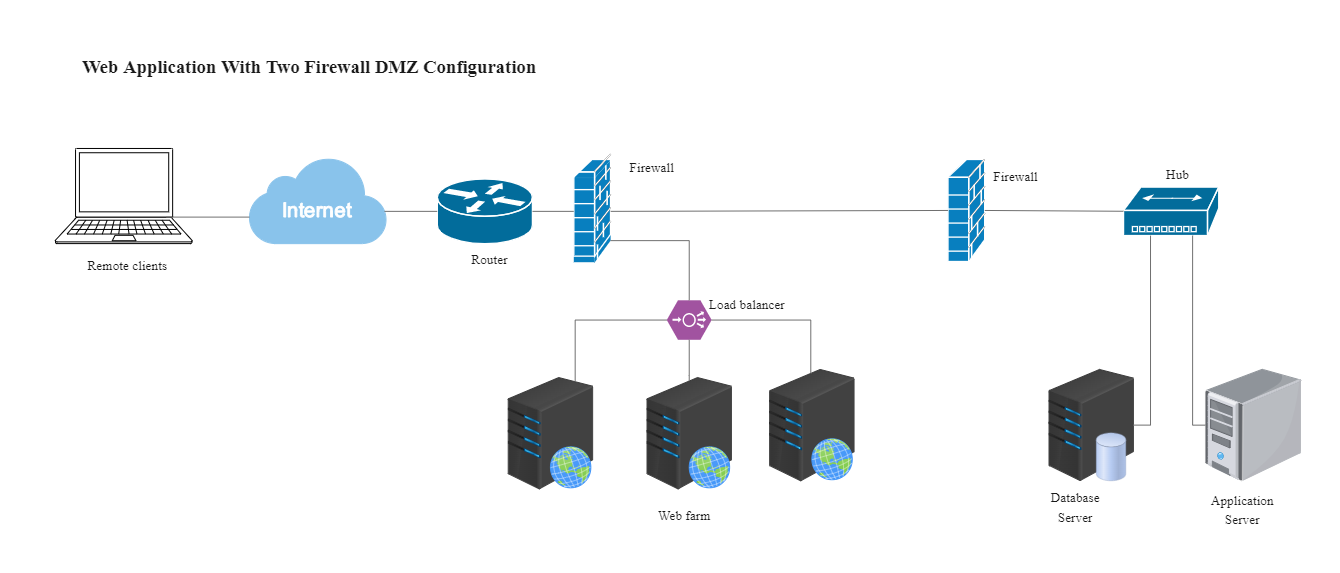
Following is the web application with two firewall DMZ Configuration. It should be noted here that the DMZ configuration is identical to the VLAN configuration. There are no restrictions on the IP address or subnet assigned to the DMZ port, except it cannot be identical to the IP address given to the predefined VLANs. As the diagram illustrates, the more secure approach to creating a DMZ network is a dual-firewall configuration, in which two firewalls are deployed with the DMZ network positioned between them. Here, the primary firewall is for DMZ and the internal network. As stated above, this gives an extra layer of security because two devices need to be compromised for an attacker to gain access to your internal network.
Tag
business
chart
education
Share
Report
0
611

Post
Recommended Templates
Loading
